The following section compares Windows NT features with those of UNIX, with which you are already familiar.
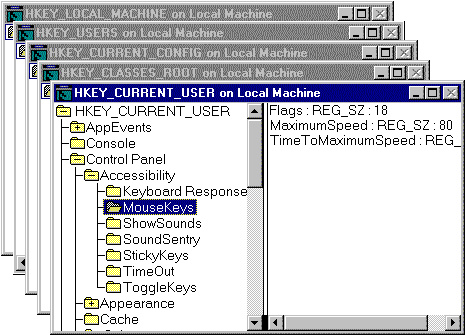
Windows NT stores security and system settings in a database called a registry. Whereas UNIX keeps its settings scattered around the /etc directory, Windows NT administration is much more centralized and generalized. Because everything important to Windows NT is stored in the registry, its integrity is essential to the system’s operation and security. Unlike the UNIX /etc files, the Windows NT registry automatically maintains a backup copy that can be retrieved.
It may help to think of the graphical user interface (GUI) administrative tools and control panel utilities as front ends to the registry, as their main function is to manipulate data in the registry. Windows NT includes several Registry Editors that enable the administrator to bypass normal administrative tools and directly modify the registry. Similar to editing files on UNIX in the /etc directory, it is important to know what you are doing when changing Windows NT registry settings, because you can destroy data or render the system unbootable.

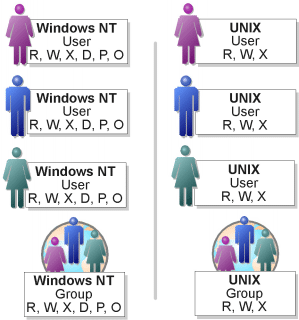
Windows NT users and groups look familiar to someone coming from UNIX, but you will soon discover that Windows NT allows much finer control over who can do what. Users represent actual people or just a set of permissions that you wish to maintain. Groups can contain individual users or other groups. As in UNIX, the strategy for user access initially allows a base-level access, adding additional levels as appropriate. The Windows NT philosophy is to create a group for users who require similar access to the same resources.
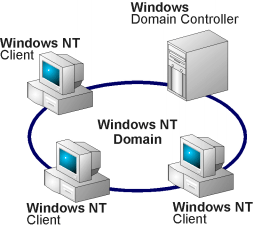
UNIX installations typically use flat files, such as etc/password and etc/group, to maintain user and group information on individual computers. When multiple UNIX computers need to be managed together, a distributed network database such as NIS/YP or NIS+ can be used. Windows NT stores user and group information in the registry and uses the Windows NT Netlogon Service to provide a network security database. As with the Network Information Service (NIS), an organization of Windows NT computers can be broken into domains or administrative groupings. Relationships can be created among domains so that users from one domain have access to resources in another without requiring the user to have an account in every domain. This relationship is called a trust in the Windows NT domain system. This is similar to the concept of host equivalence in UNIX, but with more control.
DomainsWindows NT uses domains as administrative groupings of users and computers. A single domain has a recommended limit of 40,000 users. If the domain exceeds 40,000, or the organization requires multiple administrative units, then a single domain is not the recommended configuration. Unless the organization has multiple domains, trusts are not an issue.
A complex operating system requires a sophisticated file system. The Microsoft Windows NT file system, NTFS, contains features for performance, security, and fault tolerance that are comparable to UNIX file systems. It also provides a reasonable namespace and supports large-sized files and volumes. Windows NT can also use the file allocation table (FAT) file system enabling compatibility with previous Windows operating systems, at the cost of file system security.
Most UNIX implementations only support the TCP/IP protocol out of the box. There are plenty of public domain and commercial packages that provide additional protocol support for UNIX, but they require some additional effort or installation cost.
By default, Windows NT supports TCP/IP, IPX/SPX, AppleTalk, DLC, and NetBEUI out of the box. Adding the protocols is simply a matter of installing optional software from the Windows NT compact disc. Administering the additional protocols uses the existing tools, as new menus and options are installed at the same time as the protocol.
Traditionally, UNIX comes with all the lights turned on. Even the most minimal UNIX installation usually includes network services that you do not need. Over time, these default services have become the focus of criticism of UNIX systems. The process of securing a UNIX computer involves finding out what network services it offers, and turning them off one by one if they are not needed.
For the most part, Windows NT starts with the lights turned off. It requires you to take specific steps to access services on the network. You would typically install only services that you are going to need.
Although the Windows NT security system looks more complex than a typical UNIX installation, it is more intuitive. However, there are areas, like security concepts, where you may struggle. For example, the Windows NT domain system concept of global versus local users and groups is not readily comprehensible, and the implications of file system permissions take some experimentation to understand. Ideally, one should experiment with Windows NT security features in a small, controlled situation before trying to implement them on a large scale.
The NTFS file system has a more complex security mechanism than the traditional UNIX file system permission bits. NTFS files and directories have access control lists (ACLs) that control resource access at the user level.
In UNIX, the effective privileges of a user or group depend heavily on the file permission bits, and therefore what programs they can run and what files they can access. UNIX security also tends to be an all-or-nothing approach, with either unprivileged users or "superusers." Finer control of access levels requires more experienced systems administrators and knowledgeable users.
Windows NT associates specific rights with users and groups. These rights match actions that users may wish to perform, such as backing up files and directories. This enables you to distribute permissions as needed, without giving away the entire system.
The logging facility most often used in UNIX is syslog. Windows NT refers to logging as auditing and the log messages as events. Events are stored in a binary format and are viewed with the Event Viewer program. Events can be exported into ASCII form for UNIX traditionalists and imported into other programs, such as a database or spreadsheet.
Windows NT processes will look familiar to UNIX administrators. As with UNIX daemons, Windows NT has processes that are started at boot time and run until the system is shut down. There are tools for displaying which processes are running and what resources they are using. The Windows NT equivalent of a UNIX daemon is called a service. A service plays a specific operating system role, just as in UNIX. For example, the Windows NT Scheduler service executes scheduled jobs, like the cron daemon in UNIX.
A service can be started, stopped, restarted, paused, and resumed from the GUI or command line.
UNIX provides the infrastructure of Internet messaging. Traditionally, this has been the role of the Sendmail program. There have been several large-scale messaging systems for computer operating systems, but they were usually restricted to the LAN and relied on a UNIX computer to provide connectivity to other mail systems on the Internet. Windows NT can run the Microsoft Exchange server to provide e-mail for the corporate LAN environment and use the Internet Mail Service to speak SMTP to the Internet. There are also third-party implementations of Sendmail for Windows NT that leverage your experience with Sendmail on UNIX.
Most UNIX sites use dedicated remote-access devices to provide dial-up access to their UNIX computers. It is possible to use multiple-port serial boards in both UNIX and Windows NT servers, but these are usually limited to low-end or small sites. Windows NT comes with remote-access services as part of the base operating system, while most UNIX versions only support PPP as an add-on and are not expected to be used to create large dial-in facilities.
Administrators new to Windows NT generally spend all their time using the GUI administration tools. As administrators become more experienced, they discover that more efficiency can be gained by using the command line. Quite a bit of Windows NT administration can be done from the command line, and UNIX administrators are more comfortable here than their Windows counterparts.
With most versions of UNIX, you can perform anything on a remote computer in the same manner as on a local computer. Remote administration is as simple as opening an rlogin, telnet, or X Windows session on a remote computer.
One of the first questions a UNIX administrator may have is, "How do I administer Windows NT without standing in front of the computer?" With Windows NT, the ability to remotely administer a computer depends on the functionality offered by the program you are using. Some administrative programs perform equally well remotely as locally. Some perform a reduced set of operations remotely, and others have no ability to network. Consequently, third-party developers offer numerous remote-control packages that essentially display the console of a remote Windows NT computer on the local computer. Using this method, you can do almost anything at the console, including sending keyboard sequences such as CTRL+ALT+DEL to mimic a local keyboard.
©1997 Microsoft Corporation. All rights reserved. Legal Notices.
Last Updated: December 1, 1997