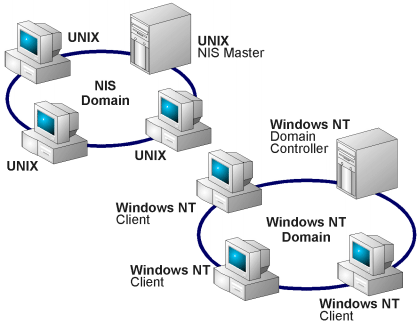
UNIX uses flat files (etc/password and /etc/group) to maintain user and group information on each computer. This quickly becomes unmanageable when more computers need to share file systems or other resources. For example, if a user changes his or her password on one computer, the change is not shared with the others. Sun Microsystems, Inc. developed a networked distributed database called Yellow Pages (YP), which was later renamed the Network Information Service (NIS). It coordinated and synchronized UNIX flat files among multiple computers arranged in administrative groupings called domains. NIS+ introduced a hierarchical structure to NIS domains as well as increased flexibility and complexity.
Windows NT stores user and group information in the registry and also allows you to administer each computer individually. The end result is the same as in the UNIX model, security coordination and synchronization become unmanageable with only a few computers.

The Windows NT domain system provides a networked security database for Windows NT. Similar to NIS, a group of Windows NT computers can be organized into domains or administrative groupings (see Chapter 1, Microsoft Windows NT from a UNIX Perspective).
YP/NIS users are familiar with the concepts of master and slave (or replica) servers. The master servers store the database, while the slave servers copy it from the masters. This provides some redundancy and load balancing to the network database because there is no single-point-of-failure. The Windows NT domain system has similar goals with the Domain controller (DC). A Primary Domain Controller (PDC) is the repository of the network security database for a single Windows NT domain. A Backup Domain Controller (BDC) serves as a backup or alternate if the PDC becomes unavailable. If needed, DC roles can be changed by the administrator.
Windows NT offers an intermediate step between chaos and domains in the form of Workgroups. Workgroups are logical groupings of a small number of computers. While they provide structure, workgroups do nothing to centralize security administration. Workgroups are also not very useful on networks that contain routers and wide-area links because of the traffic that would have to pass through the routers.
Administrators new to Windows NT will find a considerable increase in complexity when administering a domain. This may lead you to an initial tendency to avoid setting up your Windows NT computers as domain controllers. However, you will quickly discover that most Windows NT administration assumes you are using the domain system, and it will be to your advantage to use it from the start rather than avoid it. You will need to reinstall your Windows NT servers when changing them from standalone servers to domain controllers.
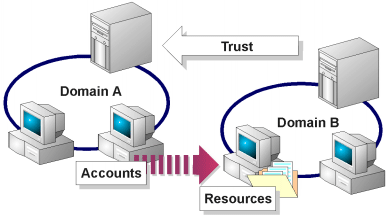
If you want to allow users from one UNIX computer to access resources on another UNIX computer, but want to avoid duplicating all password and group information, you can use the host equivalence mechanism. This allows you to specify a list of remote computers that are trusted by the local computer to treat their users as if they were local users. The Windows NT security domain system has a similar concept called trusts. You can create trust relationships among Windows NT domains that allow users to access resources in domains where they do not have accounts. Unlike UNIX, both domains have to give each other permission to do so. The domain allowing access to users from another domain must be configured to trust the other domain, and the domain being trusted must be configured to allow it to be trusted by the other domain. Trust relationships can also be bi-directional, where users from either domain can access the other.
©1997 Microsoft Corporation. All rights reserved. Legal Notices.
Last Updated: December 1, 1997